Describe What Encryption Is and Why It Is Used
In 700 BC the Spartans wrote important messages on leather which was wrapped around sticks. Encryption is a technology that conceals data using complex algorithms.
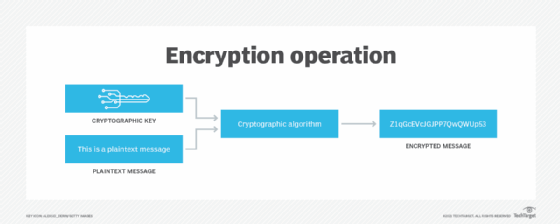
What Is An Encryption Key Definition From Searchsecurity
The science of encrypting and decryption information is called cryptography.

. Encryption is a form of technology that allows concealing data from others using advanced algorithms known as ciphers to turn normal plain-text data into unreadable data. Network encryption network layer or network level encryption. The key size is independent of the block size.
To encrypt a message you need the right key and you need the right key to decrypt it as wellIt is the most effective way to hide communication via encoded information where the sender and the recipient hold the key to decipher data. Encryption uses an algorithm to scramble or encrypt data and then. The public safety community increasingly needs to protect critical information and sensitive data particularly within land mobile radio LMR communications and encryption is the best available tool to achieve that.
The Greeks used krypto to describe something that was hidden or secret. The encryption is tied to the login identity of the user and the key is generated automatically and applied automatically. This serves to thwart cybercriminals who may have used.
With a symmetric algorithm both encryption and decryption keys are the same so the same key must be used to enable secure communication. Encryption is a process that scrambles readable text so it can only be read by the person who has the secret code or decryption key. And then theres information that you dont want other people to see.
Encryption is a form of data security in which information is converted to ciphertext. View the full answer. Encryption ensures effective security where information cannot be intercepted and used to hinder emergency response or endanger responders and the public.
Network encryption sometimes called network layer or network level encryption is a network security process that applies crypto services at the network transfer layer - above the data link level but below the application level. Authorized users systems and processes possess a cipher key which is the cryptographic specialized key that is able to unlock the unreadable data and turn it back into the. One key is used for encryption and a different key is used for decryption.
The encrypted data is called ciphertext and unencrypted or decrypted data is called plaintext. This is not possible if the data is encrypted in the first place. Previous question Next question.
It takes very little time and therefore very little money for a computer. Encryption enhances the security of a message or file by scrambling the content. A hacker cannot alter the data to commit any fraud.
It helps provide data security for sensitive information. Symmetric encryption is a commonly-used method where the encryption key and the decryption key are the same. Today the various encryption methods fall into one of two main categories.
Symmetric-key encryption and asymmetric encryption. Of course only you and authorized parties should have access to this key otherwise it will defeat the. Only authorized people who have the key can decipher the code and access the original plaintext information.
The network transfer layers are layers 3 and 4. Asymmetric encryption uses two separate keys. Like your browser history wink or certain pictures you may have sent to acquaintances wink.
This is one of the backbone of data security. Encryption is a process that encodes a message or file so that it can be only be read by certain people. As a result asymmetric encryption can be more effective but it is also more costly.
If anyone makes any change to the Encrypted data the. Encryption is important because it allows you to securely protect data that you dont want anyone else to have access to. To protect locally stored data entire hard drives can be encrypted.
Encryption is a process by which data is transformed into another form or code in such a way that only people with a decryption key can understand it. An encryption algorithm is run on the plaintext along with an encryption key. A determined hacker could easily retrieve it if it is not properly wiped.
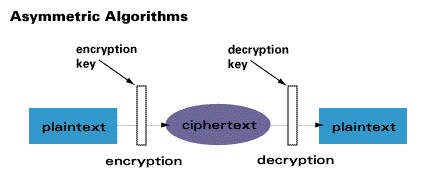
Often a public key is used to encrypt the data while a private key is required to decrypt the data. Vast amounts of personal information are managed online and stored in the cloud or on servers with an ongoing connection to the web. However there are some other subtle differences as well.
That means that an A becomes a Z B becomes a Y etc. While data Encryption stops anyone from reading the data one other major benefit of Encryption is that once done. An encryption key is a number character or string of characters that.
Encryption is a process used to protect data by using a key to scramble it so that only someone with the correct key can read the data. What is Encryption. Encryption can prevent blackmail.
Businesses use it to protect corporate secrets governments use it to secure classified information and many individuals use it to protect personal information to guard against things like identity theft. The private key is only given to users with authorized access. I wont bore you with the ins and outs of encryption so in a nutshellEncryption is the method of converting information stored in plain text this blog is an example of plain text into secret code that hides the informations true meaning.
The decryption key is kept private hence the private key name while the encryption key is shared publicly for anyone to. Encryption makes data unreadable while decryption makes unreadable data readable by converting it back to its original state. Encryption Ensures Integrity of Data.
The key is used by the encryption algorithm when it is encrypting the plaintext. Symmetric algorithm encryptions are commonly used for bulk data encryption and are fast and easily implemented by hardware. A public key and a private key.
In asymmetric or public key encryption there are two keys. The biggest difference between encryption and decryption is what happens to the data in question. In even simpler terms encryption is a way to render data unreadable to an unauthorized party.
This type of encryption used a reversed-alphabet simple substitution code. Users who are protecting their data through encryption will receive a cipher key. This is a specialized key to unlock the data so the material is readable again.
There are two types of encryption algorithms. The following are some major benefits.
Cryptography Defined Brief History


No comments for "Describe What Encryption Is and Why It Is Used"
Post a Comment